REDMOND, WA - Cybersecurity experts have noted a large increase in the number of phishing attacks recently as hackers have been altering their attack avenues in order to work their way around increasingly complex email security systems designed to circumvent their efforts. Both the volume and complexity of malicious emails have been on the rise and are proving to be increasingly able to bypass Secure Email Gateways (SEGs) such as Microsoft and Proofpoint, according … [Read more...]
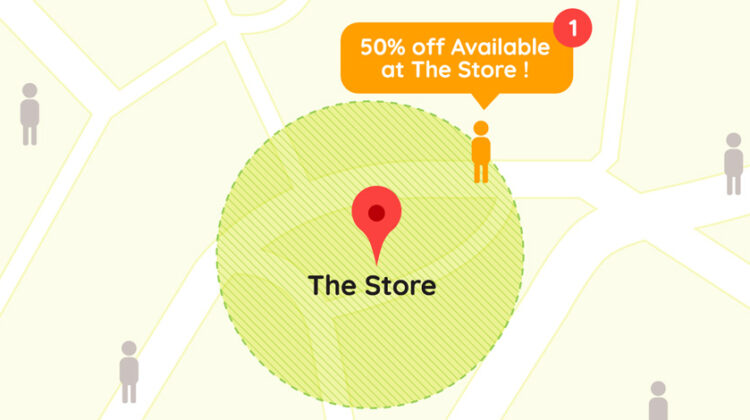
What Is Geofencing And How Does It Work?
FLORIDA - Geofencing is a location-based technology that creates virtual boundaries around a specific geographic area. These boundaries are defined by GPS, RFID, Wi-Fi, or cellular data. When a device, typically a smartphone or GPS-enabled device, enters or exits the predefined geographic area, it triggers a response or action. Here's how geofencing typically works: Imagine a virtual fence you can draw around any area, like your competitor's dealership or even … [Read more...]