
WEST PALM BEACH, FL – A new study has revealed that consumer email addresses are being collected by online login, registration, and newsletter subscriptions even before the user has manually submitted the form or even given their consent to have their personal information collected, igniting controversy over privacy rights – or lack thereof – on the internet.
The goal of the study was to spot sites that pulled email and password information before users could submit a consent form. This means if you type something out in a form on some websites and then erase it before hitting enter, some services may still collect what you typed.
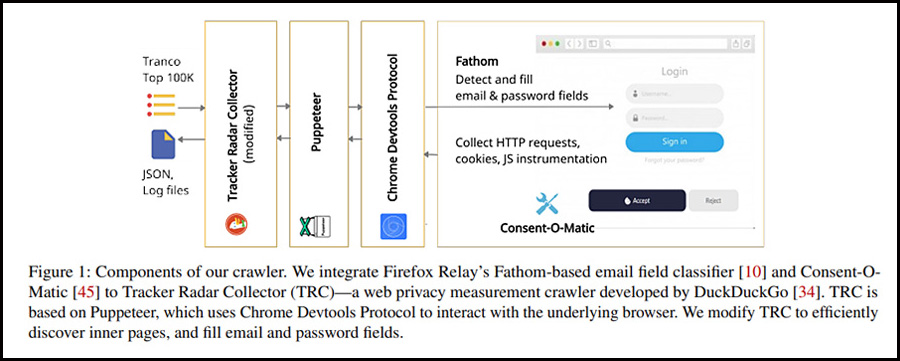
LEAKY FORMS STUDY
A Study of Email and Password Exfiltration Before Form Submission conducted research of 100,000 websites, and discovered that domain addresses are essentially being harvested – without user knowledge – by 2,950 websites based in the United States, along with an additional 1,844 websites in the European Union. [Leaky Forms: A Study of Email and Password Exfiltration Before Form Submission (FULL STUDY – PDF / Pages: 18)]
The study indicates that the majority of the collected web addresses – again, which are taken before they are actually submitted, giving the user no opportunity to change their mind – are then transmitted to known tracking domains.
However, 41 additional destinations that emails were being sent to are not listed amongst any known blocklists – leaving their potential use completely unknown – and an additional 52 websites utilized incidental password collection by third-party session replay scripts.
The controversy in these situations arises from the fact that many individuals – 81 percent, according to a recent survey – who fill out online forms often will abandon them and back out, believing that because they have not submitted the information that it was not transmitted. 51 percent of survey respondents indicated that they had done this at least once in the past month alone.
Collecting personal information without receiving consent from the user, experts say, would result in regulations governing such activity to be greatly tightened if the practice generates enough furor among those who frequent the internet.
THE TOP TEN CULPRITS
According to the Leaky Forms study, the top culprits when it comes to the harvesting of user personal data without consent include:
- usatoday.com
- trelio.com
- independent.co.uk
- shopify.com
- married.com
- newsweek.com
- prezi.com
- branch.io
- proothomalo.com
- codeacademyazcentral.com
The study concluded that this form of data collection could result in serious identity theft issues and other maladies, and that oversight needs to be implemented in order to keep web users safe.
Considering its scale, intrusiveness and unintended side-effects, the privacy problem we investigate deserves more attention from browser vendors, privacy tool developers, and data protection agencies,” the Leaky Forms authors said.

About The Author: John Colascione is Chief Executive Officer of SEARCHEN NETWORKS®. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a how-to book called ”Mastering Your Website‘, and is a key player in several online businesses.

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
this is “standard practice” for modern tech, although not highlighted. Check modern form service providers — they literally have to offer the feature in order to be competitive.
It is the deployment that is regulated (and should be, imho). I turn it off unless my deployment would be fine with it on… based on law, ethics, regulation, and my desire to be liable for the info stored on servers somewhere.
People should not be shocked that technology exists. They should instead assume technology exists and will not be misused, and then … this is they key part …. prosecute those who misuse technology (and anything else).
We all need to grow up. Bad people are out there. We won’t get anywhere banning technology (it’ll just stay hidden) butvwe can do very well if we seriously ban explotation, abuse, etc and prosecute offenders.