WEST PALM BEACH, FL – I’ve been writing about scam emails and phishing attempts for a number of years now and although I don’t have as much time at my disposal as I used to, I still like to detail their processes when I can so people can learn how to avoid these scams while seeing and understanding how clever these little sneaks are when plotting to steal your information (and money). Past features have includes similar scams targeting customers of Facebook, GoDaddy, FedEx, Verizon, and AMEX.
Some of these scams are extremely convincing, so mush so that even I fell victim to at least one of them in the last few years, that is how good they can look. But today we will look at a not so clever, but good looking fake TD Bank website designed to fool customers. It’s not a very sophisticated Phishing attack, as the URL of the site is not being cloaked, hidden or other wise covered up, but the design of the fake website I felt looked high quality enough to fool a large number of visitors.
Let’s take a look at the scam as it is intended to ruin you.
First you receive an email which cleverly does not go to your spam box but is indeed spam. This is often done by hacking a hosting account (website) which has a good reputation, history and is not on an email blacklist, so the entire purpose of hacking the website, is really to access the ability to send spam from the websites whitelisted IP address.
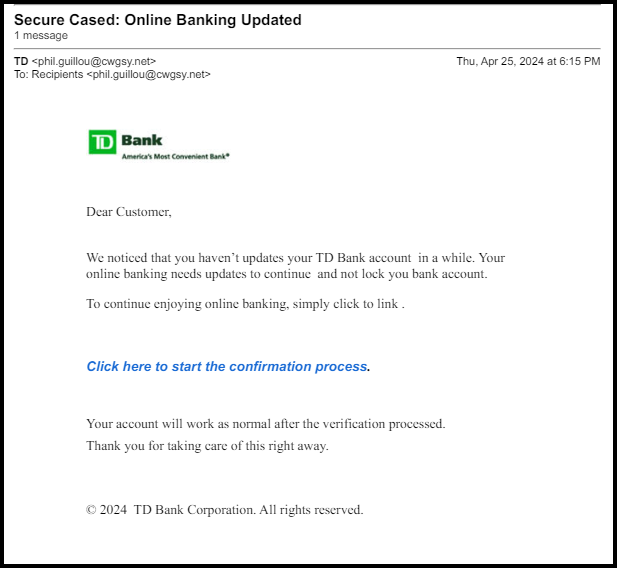
The emails will often include many spelling and grammar errors which should be a dead giveaway, however, often times, people do not take time to read things carefully and they just quickly click on links. This is the worst thing you can do when reading email.
You should consider this fact: 91% of cyberattacks start with an email.
Phishing remains the number one attack vector, according to a new study that analyzes why users fall for these lures. The majority of cyberattacks begin with a user clicking on a phishing email.
Clicking on the link in this email will bring you to this next page, which is probably designed to give the appearance that the website has the intention to maintain a secure environment.
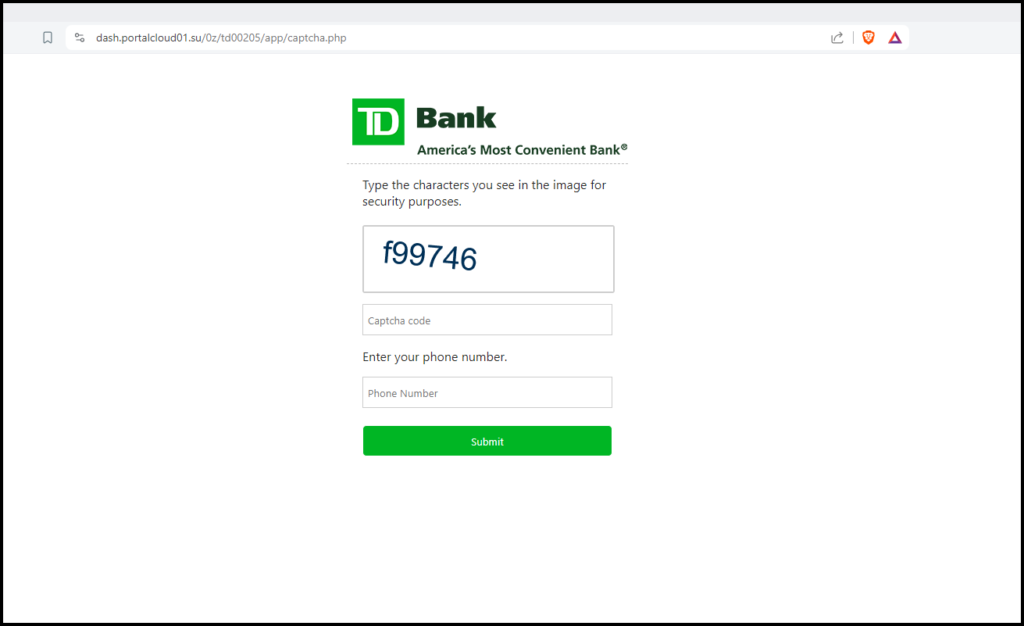
Filling out the captcha code correctly will bring you to the next page.
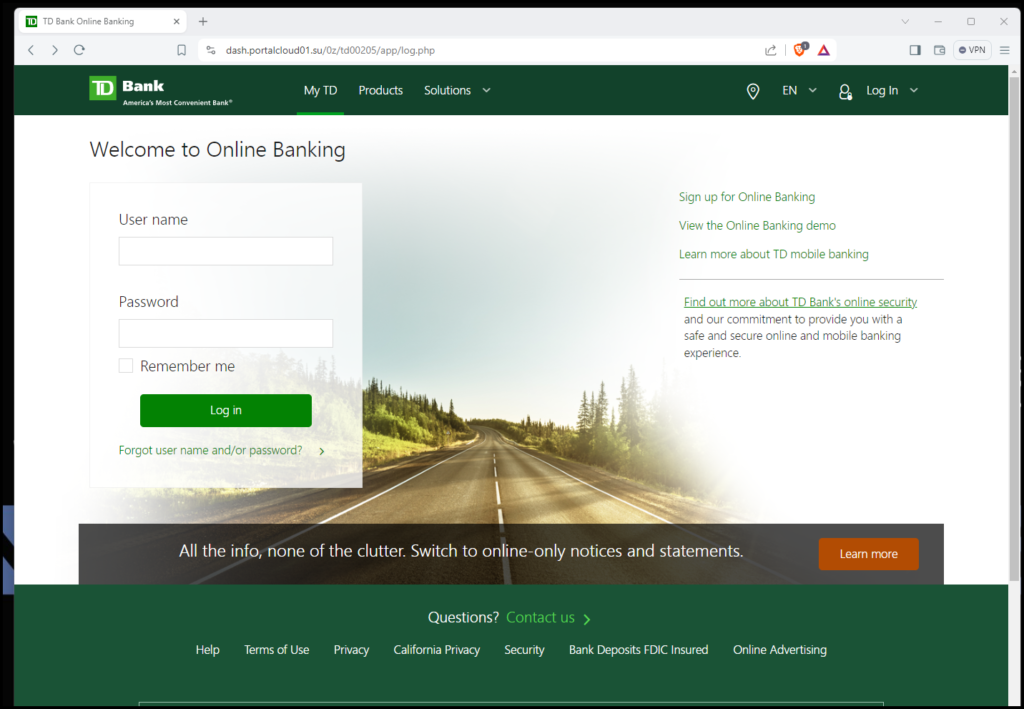
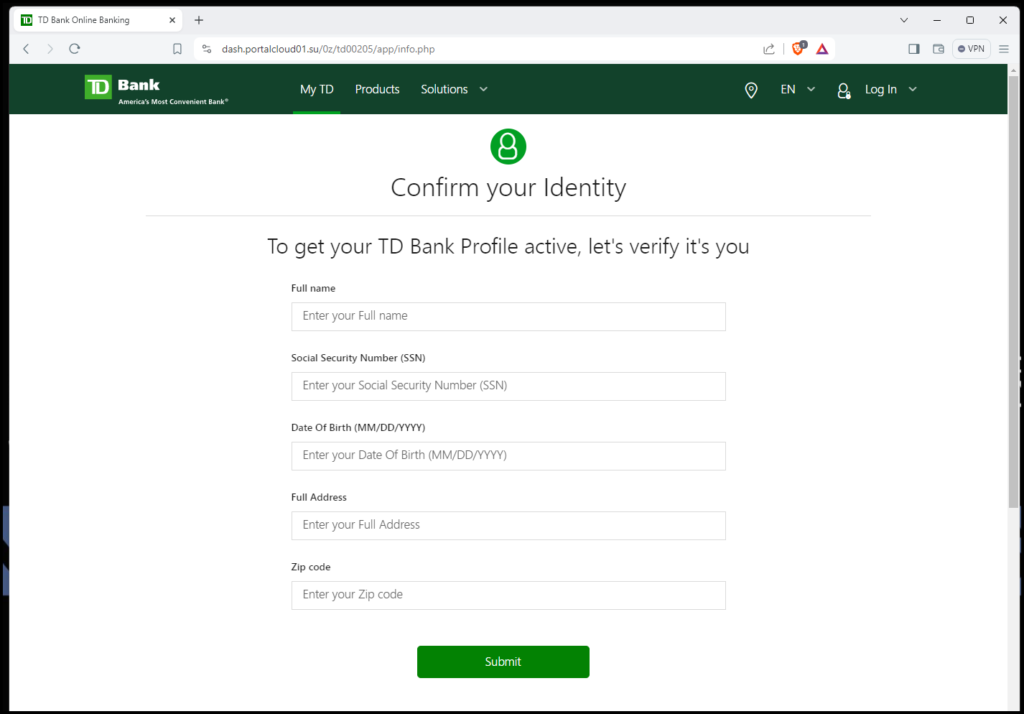
This page is designed to capture your username and password. As you can see if you look in the address bar, dash.portalcloud01.su is NOT an official TD Bank website address. This is why I’m considering this instance a very primitive fake Phishing website.
After filling in your username and password, which is immediately emailed to a hacker looking to get into your real TD Bank account, you are presented with this page.
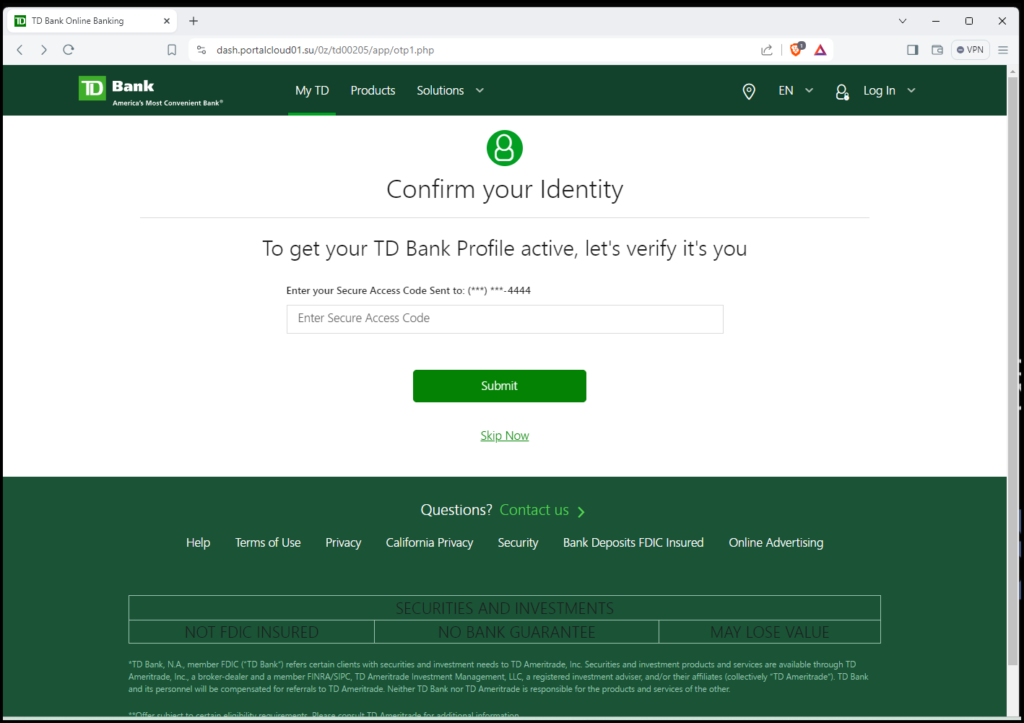
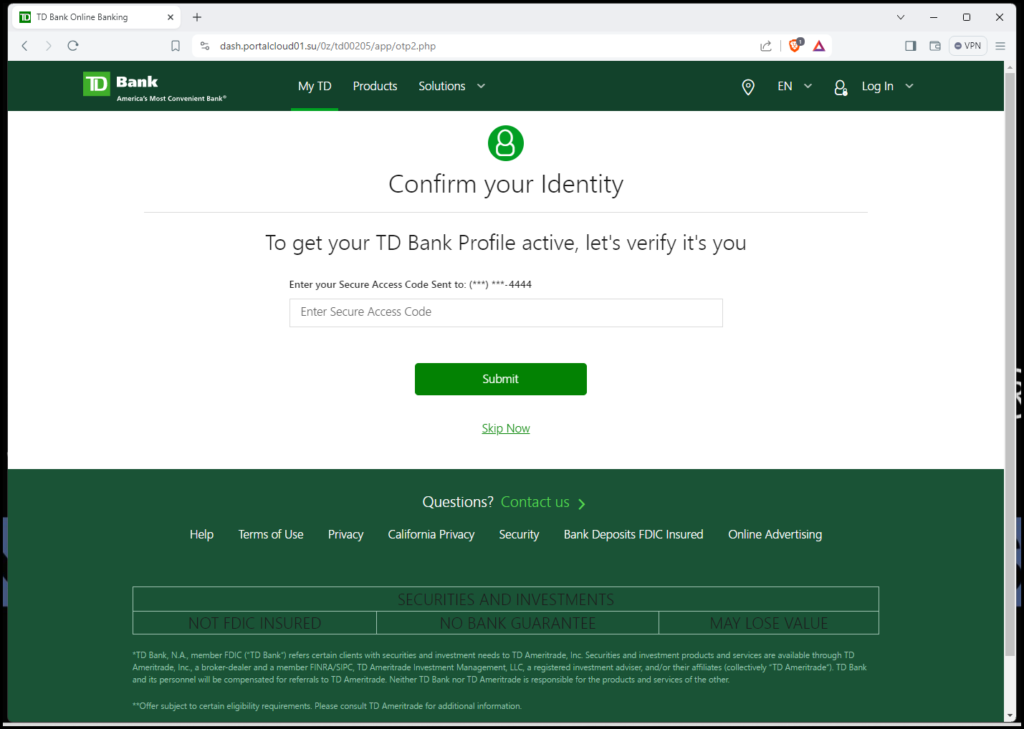
Now, what is likely happening at the time you are sitting staring at this screen above, a hacker is logging into your real TD Bank account online. They have the correct username and password, because you just entered it into their fake website and they just received it. So when they attempt to login to your real TD Bank account, TD sends you a text message to verify it is you. This page will allow you to enter the code so that too could be sent to the hacker. The hacker can now use it to gain access to your account.
Next you will see this page which designed to steal some more information, while more importantly, buying more time in case the hacker did not get the first text in time; The hacker can get better situated and use this page to prompt you again for another text.
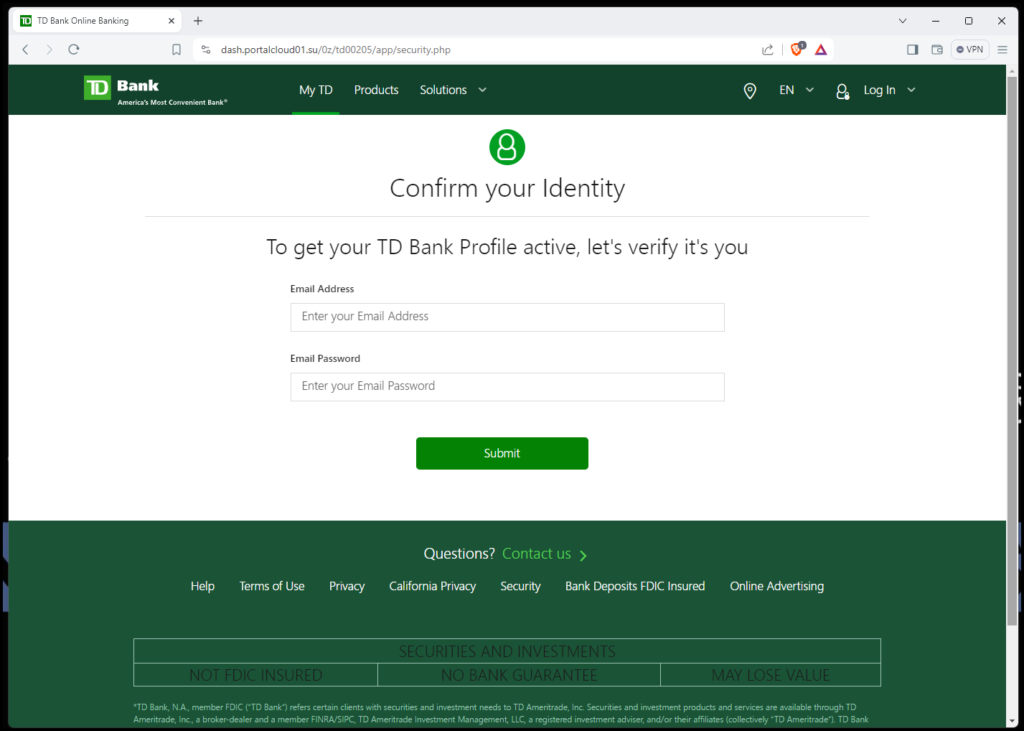
Next you will see this page again.
This will ensure the hacker gets the text in time, because he or she already received an alert a few minutes ago, but was not ready. This process will give them another shot in case something went wrong the first time.
By this time, you will be compromised.
Older versions of this scam would bring you to the real TD Bank website after you entered the username and password, so you would not realize what site you were just on, and figure you mistyped it, but now with Two Factor Authentication (verify by text message) needed, the scam needs to continue to additional pages to receive the text-message code.
It took me about a week to write this up from the time I saved these screenshots. By the time I did write this, the scam located on dash.portalcloud01.su was already finished and gone.
The scammers have a very limited time to fly under the radar and run these scams. After enough users report the scam to their internet service provider ISPs and/or mark the emails as spam, the hackers will loose their Whitelist status to bypass filters that attempt to keep people safe from these types of nefarious tactics.

About The Author: John Colascione is Chief Executive Officer of SEARCHEN NETWORKS®. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a how-to book called ”Mastering Your Website‘, and is a key player in several online businesses.

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
Leave a Reply