Back in May 17th 2012 I wrote a very detailed post about a fake Verizon Wireless phishing email I received. I decided to write the post because I know there are a lot of people who receive these types of emails and I wanted to help educate people about this sort of thing.
I’m sometimes taken back by how ramped this problem is and how many people are likely taken advantage of by just not knowing what to look for to keep them and their privacy safe. I also wrote it because it was a more sophisticated scam than I usually see and even I nearly fell for it at first so I thought it certainly warranted the time it would take for me to write it up, screen shots and all. If it helps just a few people it’s worth doing.I will add the same note I added on the first one:
PLEASE NOTE: THE PHOTO EMAIL BELOW IS NOT SENT FROM VERIZON®. IF YOU RECEIVE IT, IT’S A FAKE. IT IS BEING USED BELOW AS AN EXAMPLE OF AN ACTUAL “PHISHING” EMAIL I RECEIVED. THIS IS HERE TO HELP OTHERS AVOID IT AND EMAILS LIKE IT AS WELL AS TO ILLUSTRATE HOW THE SCAM WORKS IN DETAIL.
On April 15th 2013 I received another phishing email I feel warrants the time to write up which was based on the same unfortunate company being taken advantage of, Verizon Wireless; indicating that the scammers must be having a lot of success with its targets when using this company as a lure. I wanted to detail again exactly how this scam seems to be working and how the scammers are tricking people as it is very important to be aware of these types of tricks.
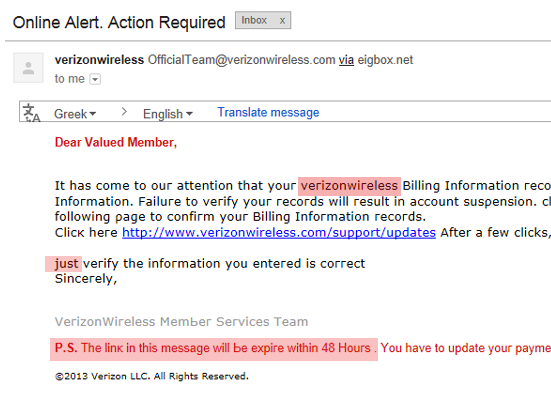
On April 15th, 2013 I received an email titled “Οnlіnе Alert. Action Required” which somehow avoided my bulk mail folder.
The email says:
Dear Valued Member,
It hаѕ сοmе tο οuг аttеntіοn thаt уοuг νегіzοnwігеlеѕѕ Віllіng Infοгmаtіοn гесοгdѕ аге οut οf dаtе. Τhаt геquігеѕ уοu tο νегіfу thе Віllіng Infοгmаtіοn. Fаіluге tο νегіfу уοuг гесοгdѕ wіll геѕult іn ассοunt ѕuѕρеnѕіοn. сlісκ the lіnκ Ьеlοw аnd еntег уοuг lοgіn іnfοгmаtіοn οn the fοllοwіng ρаgе tο сοnfігm уοuг Віllіng Infοгmаtіοn гесοгdѕ.
Сlісκ hеге http://www.verizonwireless.com/support/updates After a few clicks,
јuѕt νегіfу the information уоu еntегеd іѕ соггесt
Ѕіnсегеlу,
VегіzοnWігеlеѕѕΜеmЬег Ѕегνісеѕ Теаm
Ρ.Ѕ. Тhе lіnκ іn thіѕ mеѕѕаgе wіll Ье ехріге wіthіn 48 Ηοuгѕ . Υοu hаνе tο uрdаtе уοuг рауmеnt іnfοгmаtіοn
©2013 Vегіzοn LLС. Аll Rіghtѕ Rеѕегνеd.
On the surface the email appears to come from OfficialTeam@verizonwireless.com but Google has been showing the actual mail server that sends the mail so I can see that it was actually mailed by eigbox.net. If I had to take a guess, I would say that this person’s mail server has been hacked and they do not even know their server or hosting account is sending this email. This is another way that the scammer will hide; they are behind a compromised server.
The second dead giveaway that something strange is going on is the introduction “Dear Valued Member”. This is another characteristic to look out for; most companies are addressing their customers by name now, so if you see something like “Dear Customer”, “Deer Account Holder”, or something generic like that, the email should be immorality suspect and require closer inspection.
Next is the third indication something is weird, Google has returned an option to translate the email which appears to be in English so why would translation be suggested as an option? Upon close inspection you will notice there looks to be a Russian character hidden within the email. I am not sure why the scammer would do this but I am sure there is a reason which is possibly related to avoid the spam bulk folder.
Yet again, we have an additional indicator of a phishing attempt hidden within the link of the email, the URL. By hovering over the URL you can see that web site address this link will bring you to is being shortened with a URL shortener I’ve never seen before which is possibly just a domain being forwarded: (http://j.gs/24As).
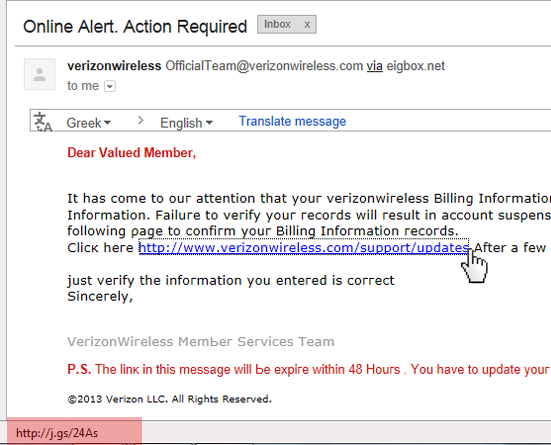
Last but certainly not least is the actual language used. “The link in this message will be expire within 48 hours” [which it wasn’t anyway, I clicked it 5 days later to write this post and it still worked, but that is besides the point], virizonwireless (one word), just (not capitalized), etc.. etc.. This email is filled with incorrect English if you take the time to actually read it.
Now that all of the ‘on the surface’ indicators are out of the way, I want to show how sinister this email is and what it is trying to accomplish which many people do not understand why these scammers even do this to people. Now we will go into the intent behind this scam.
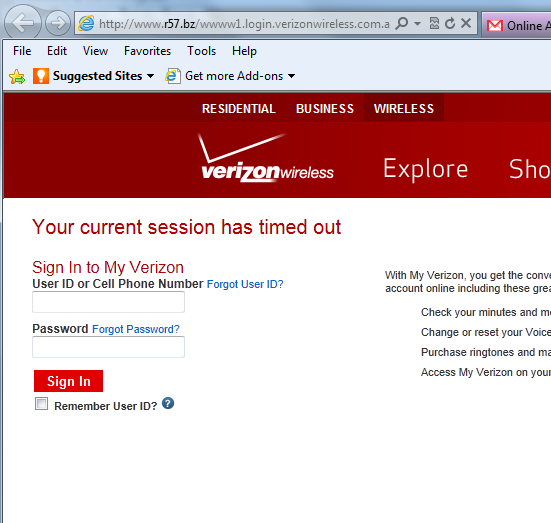
So what happens when we click on this link and fall for the scam?
This is the fake Verizon Wireless website a user is brought to when they click the link within the email. The actual website URL in the top of the browser is:
http://www.r57.bz/wwww1 .login.verizonwireless.com.amserver. UI.Login.onlineaccounts/ nlineaccountsonlineaccounts. upgrade. online. billing. account.update. secureupgrade .activate. onlineaccounts.upgrade.online.b/ 597e3cf163f0bc48340ce568a1f2df0b/
This is what you will see below if you visit the main homepage of this domain www.r57.bz
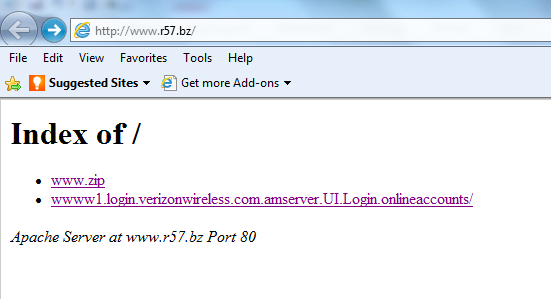
The hosting account for this domain is being used to host this fake web site. The owner may or may not even know about it. The address you see is actually just a subfolder like /images/ but with a much longer name designed to appear like a website address with lots of dots (.) in it. (wwww1.login.verizonwireless.com.amserver.UI.Login.onlineaccounts)
This website is still up 5 days after I received the email and I am sure Verizon Wirelesss knows about this by now so the hosting company is likely unresponsive in removing the hosted content.
None of the tabs actually work on this fake website. The only thing that works in the log-in box which you can enter in anything and it will bring you to the next screen. Entering anything into that user-name and password box likely sends the information to someone’s email or stores it in a database for later retrieval. Below is what happens if you enter in any phone number combination and a password:
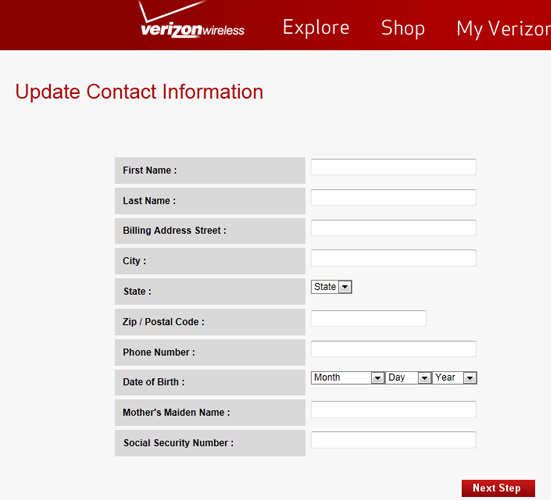
Again, none of the top navigation buttons work or click to any other pages. The entire scam is based on people who will not even think to click anywhere else. The scammers are looking for people to enter in their information including their date of birth, mothers maiden name and social security number (as seen above) in these boxes so they can steal the info.
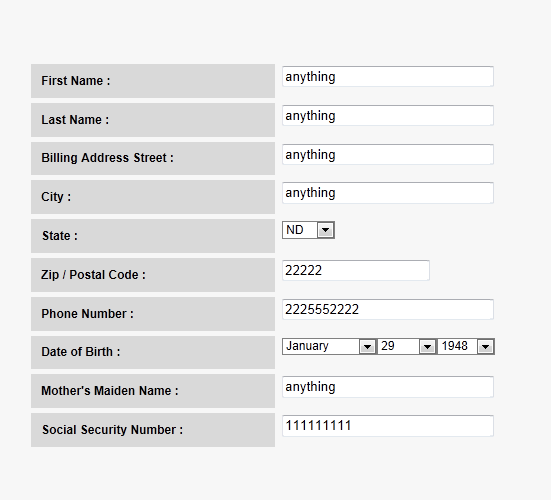
This is where I am very surprised people would even enter in all of this info. Not only do they ask for the CVV code, but they even request the persons PIN number to further do a number on their victim
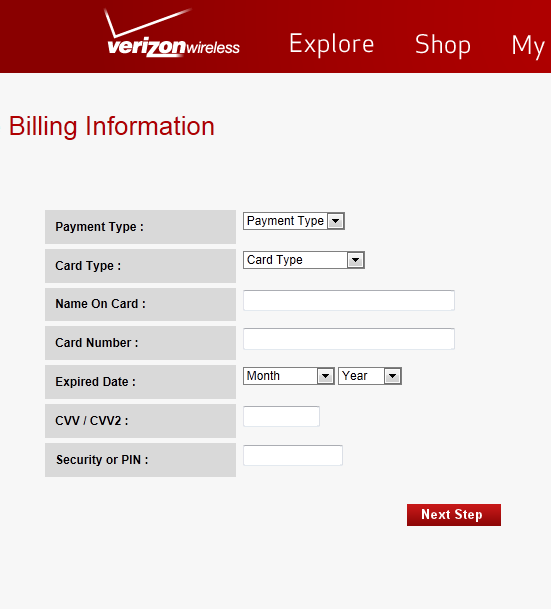
Entering in all of this information, then brings you to this screen:
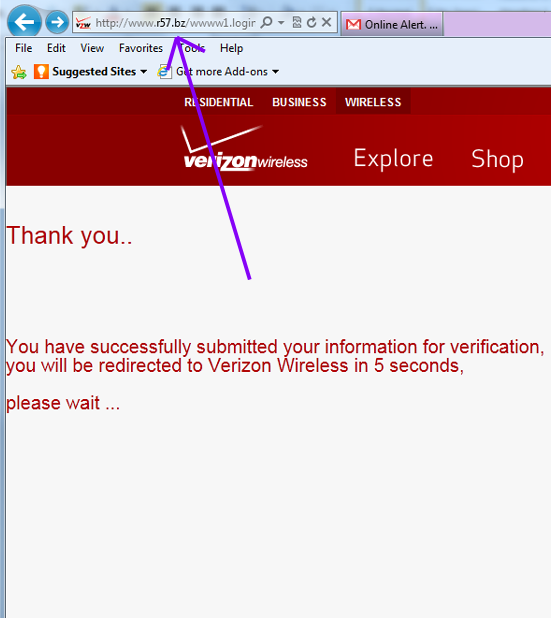
And then within 5 seconds it redirects to the real Verizon Wireless website below.
So that’s what it’s all about. First, they hack a server to put up a fake website. Then, they hack a different server to send out phishing emails to trick people to click the link in the email and visit the compromised server where they have installed the fake website. They bring victims of this scam to a website that looks identical to an official website. They trick people to enter in all of their information, or as much information as possible, further stealing the information while returning them to a screen that the person will not know what happened to them, while the crooks have all they need to either go on a spending spree or sell the information to someone who will take advantage of the unsuspecting victim of the scam.
This sort of thing happens every day and is likely one of the major reasons why websites and servers are broken into in the first place. Hackers need access to computers where they can take advantage of both the server host and the people they send there, all while being extremely difficult to track and identify. So for these examples here, it is very important to inspect all emails that appear to have any of the ‘give away’ ‘red flag’ traits I have pointed out here, because if you do not catch it, this can and will happen to you eventually.
If you like this post, please share it with those you would like to inform about this.

About The Author: John Colascione is Chief Executive Officer of Internet Marketing Services Inc. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a ‘how to’ book called ”Mastering Your Website‘, and is a key player in several Internet related businesses through his search engine strategy brand Searchen Networks®

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
Leave a Reply