NEW YORK, NY – This is the most dangerous and convincing phishing trick I have ever seen before. It’s so amazingly horrible it will fool even the smartest computer users and it’s an issue that all browser companies should be fixing immediately. Browsers should be updated to prevent these Unicode domains from being translated.
Once again our friends at WordFence are keeping all of us safe with critical information on this phishing trick and helping build awareness about it.
This is just horrendous. Horrendous!
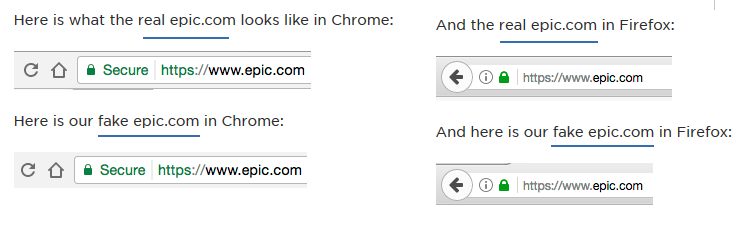
To see what is going on simply click this link https://xn--e1awd7f.com.
If you’re using Chrome or Firefox it is going to look like ‘epic.com’ and it is going to show up as being secure.
THIS MEANS THAT ANY LINK YOU VISIT FROM ANYWHERE, EMAIL, A WEBSITE, ANYWHERE NOT DIRECTLY TYPED IN, – COULD BE FAKE. YOU NEED TO BE SURE YOU ARE ON THE AUTHENTIC SITE BEFORE YOU LOGIN ANYWHERE, AND A SECURE LOCKED HTTPS ADDRESS-BAR NO LONGER MEANS YOU’RE SAFE.
The article below from WordFence will show you how to change a setting on your Firefox browser to prevent these URLs from working or translating the Unicode. If you have Chrome, there is no fix yet.
Chrome and Firefox Phishing Attack Uses Domains Identical to Known Safe Sites

About The Author: John Colascione is Chief Executive Officer of Internet Marketing Services Inc. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a ‘how to’ book called ”Mastering Your Website‘, and is a key player in several Internet related businesses through his search engine strategy brand Searchen Networks®

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
It’s sad to see phishing cases like this. There has to be something that can be done to better identify IDN’s in browsers. It would be beneficial for them to implement a security icon when an IDN is detected automatically that alert users that the URL is in fact, an idn domain. It shouldn’t be that hard to do. They can auto detect them using the same technology that detects SSL’s.
I agree very very sad; I almost couldn’t even write about it becuase it was like a through-in the towel type of vulnerability., but more people need to know about this.
This is nothing new, IDN’s have been around for years and as Eric said it shouldn’t be hard for big game broswer developers to implement an IDN ‘light’, when visiting an IDN domain, the same way the green ‘https://’ lights up for an SSL.
I do feel sorry for the people buying these domains on marketplaces where they think they are getting what they see and not what it really is eg. x– (punycody)
Damn! You are right, this is simply incredible/terrible.
This simply means you cannot even trust the domain you see in the address bar, ouch!
“Chrome has just released version 58.0.3029.81. We have confirmed that this resolves the issue and that our ‘epic.com’ test domain no longer shows as ‘epic.com’ and displays the raw punycode instead, which is ‘www.xn--e1awd7f.com’, making it clear that the domain is not ‘epic.com’. We encourage all Chrome users to immediately update to the above version of Chrome to resolve the issue.”
https://www.wordfence.com/blog/2017/04/chrome-firefox-unicode-phishing/
That’s why we educate people not to click on a link from any an email.
As seen on Facebook just now.
Someone try to sell ca.com (but its IDN xn--80a7a.com)
https://bitify.com/auctions/download-bots/domain-name-ca-com-for-sale-1019067/